Fiddler is a Web Debugging Proxy which logs all HTTP(S) traffic between your computer and the Internet. Fiddler allows you to inspect all HTTP(S) traffic, set breakpoints, and 'fiddle' with incoming or outgoing data. The most advanced API tool for Mac. Paw is a full-featured HTTP client that lets you test and describe the APIs you build or consume. It has a beautiful native macOS interface to compose requests, inspect server responses, generate client code and export API definitions.
| Join hundreds of InfoSec professionals at our upcoming [Global AppSec DC, September 9-13] and [Global AppSec Amsterdam, September 23-27] |
This page contains content that is outdated and is no longer being maintained. It is provided as a courtesy for individuals who are still using these technologies. This page may contain URLs that were once valid but may now link to sites or pages that no longer exist.
Please use the newer Edition(s) like OWASP Zed Attack Proxy Project
Dec 13, 2011 - Added on-screen menu (click on web page to open the menu to select the proxy tool menu) - Added IE9 browser to proxy tool user agent. - Added the http referrer option to allow for 'push' the http referrer automatically. The OWASP Zed Attack Proxy (ZAP) is one of the world’s most popular free security tools and is actively maintained by hundreds of international volunteers*. It can help you automatically find security vulnerabilities in your web applications while you are developing and testing your applications. Fiddler is a free web debugging tool which logs all HTTP(S) traffic between your computer and the Internet. Inspect traffic, set breakpoints, and fiddle with incoming or outgoing data. A web proxy tool. Contribute to XX-net/XX-Net development by creating an account on GitHub. IPad HTTP Debugging with Charles. Then click the “Mac OS X” tab and check “Enable Mac OS X Proxy” and “Use HTTP Proxy”. Start capturing HTTP traffic. (default proxy port is 8200). The tool is free and allows packets modification on the fly. Wil May 21, 2011.
| This project has produced a book that can be downloaded or purchased. Feel free to browse the full catalog of available OWASP books. |
| This project is part of the OWASP Breakers community. Feel free to browse other projects within the Defenders, Builders, and Breakers communities. |
Welcome to the WebScarab Project
WebScarab is a framework for analysing applications that communicate using the HTTP and HTTPS protocols. It is written in Java, and is thus portable to many platforms. WebScarab has several modes of operation, implemented by a number of plugins. In its most common usage, WebScarab operates as an intercepting proxy, allowing the operator to review and modify requests created by the browser before they are sent to the server, and to review and modify responses returned from the server before they are received by the browser. WebScarab is able to intercept both HTTP and HTTPS communication. The operator can also review the conversations (requests and responses) that have passed through WebScarab.
You may also be interested in testing the Next Generation of WebScarab.
Screenshots
Here's the main window of WebScarab. Check the WebScarab Getting Started guide for more screenshots of WebScarab in action.
Overview
There is no shiny red button on WebScarab, it is a tool primarily designed to be used by people who can write code themselves, or at least have a pretty good understanding of the HTTP protocol. If that sounds like you, welcome! Download WebScarab, sign up for the mailing list on the OWASP subscription page, and enjoy! You can read a brief tutorial to explain the basic workings.
WebScarab is designed to be a tool for anyone who needs to expose the workings of an HTTP(S) based application, whether to allow the developer to debug otherwise difficult problems, or to allow a security specialist to identify vulnerabilities in the way that the application has been designed or implemented.
Download
The canonical source repository for WebScarab is at GitHub. A zip archive of the tip of tree can be downloaded here.
Historical Versions:
Alternatively, you can download older builds of WebScarab from the OWASP Source Code Center at Sourceforge. Then install them likewise:
- Linux: java -jar ./webscarab-selfcontained-[numbers].jar
- Windows: double-click the installer jar file (complete installation instructions))
Features
A framework without any functions is worthless, of course, and so WebScarab provides a number of plugins, mainly aimed at the security functionality for the moment. Those plugins include:
- Fragments - extracts Scripts and HTML comments from HTML pages as they are seen via the proxy, or other plugins
- Proxy - observes traffic between the browser and the web server. The WebScarab proxy is able to observe both HTTP and encrypted HTTPS traffic, by negotiating an SSL connection between WebScarab and the browser instead of simply connecting the browser to the server and allowing an encrypted stream to pass through it. Various proxy plugins have also been developed to allow the operator to control the requests and responses that pass through the proxy.
- Manual intercept - allows the user to modify HTTP and HTTPS requests and responses on the fly, before they reach the server or browser.
- Beanshell - allows for the execution of arbitrarily complex operations on requests and responses. Anything that can be expressed in Java can be executed.
- Reveal hidden fields - sometimes it is easier to modify a hidden field in the page itself, rather than intercepting the request after it has been sent. This plugin simply changes all hidden fields found in HTML pages to text fields, making them visible, and editable.
- Bandwidth simulator - allows the user to emulate a slower network, in order to observe how their website would perform when accessed over, say, a modem.
- Spider - identifies new URLs on the target site, and fetches them on command.
- Manual request - Allows editing and replay of previous requests, or creation of entirely new requests.
- SessionID analysis - collects and analyzes a number of cookies to visually determine the degree of randomness and unpredictability. Note that this analysis is rather trivial, and does not do any serious checks, such as FIPS, etc.
- Scripted - operators can use BeanShell (or any other BSF supported language found on the classpath) to write a script to create requests and fetch them from the server. The script can then perform some analysis on the responses, with all the power of the WebScarab Request and Response object model to simplify things.
- Parameter fuzzer - performs automated substitution of parameter values that are likely to expose incomplete parameter validation, leading to vulnerabilities like Cross Site Scripting (XSS) and SQL Injection.
- Search - allows the user to craft arbitrary BeanShell expressions to identify conversations that should be shown in the list.
- Compare - calculates the edit distance between the response bodies of the conversations observed, and a selected baseline conversation. The edit distance is 'the number of edits required to transform one document into another'. For performance reasons, edits are calculated using word tokens, rather than byte by byte.
- SOAP - There is a plugin that parses WSDL, and presents the various functions and the required parameters, allowing them to be edited before being sent to the server. NOTE: This plugin is deprecated, and may be removed in the future. SOAPUI is streets beyond anything that Webscarab can do, or will ever do, and is also a free tool.
- Extensions - automates checks for files that were mistakenly left in web server's root directory (e.g. .bak, ~, etc). Checks are performed for both, files and directories (e.g. /app/login.jsp will be checked for /app/login.jsp.bak, /app/login.jsp~, /app.zip, /app.tar.gz, etc). Extensions for files and directories can be edited by user.
- XSS/CRLF - passive analysis plugin that searches for user-controlled data in HTTP response headers and body to identify potential CRLF injection (HTTP response splitting) and reflected cross-site scripting (XSS) vulnerabilities.
Training Material
Aung Khant (YGN Ethical Hacker Group, Myanmar) has created a series of WebScarab movies which can be found here.
There are slides of the presentation 'Uncovering Webscarab's Hidden Treasures', given at the OWASP EU Summit 2008, available here.
Future development
Features will probably include:
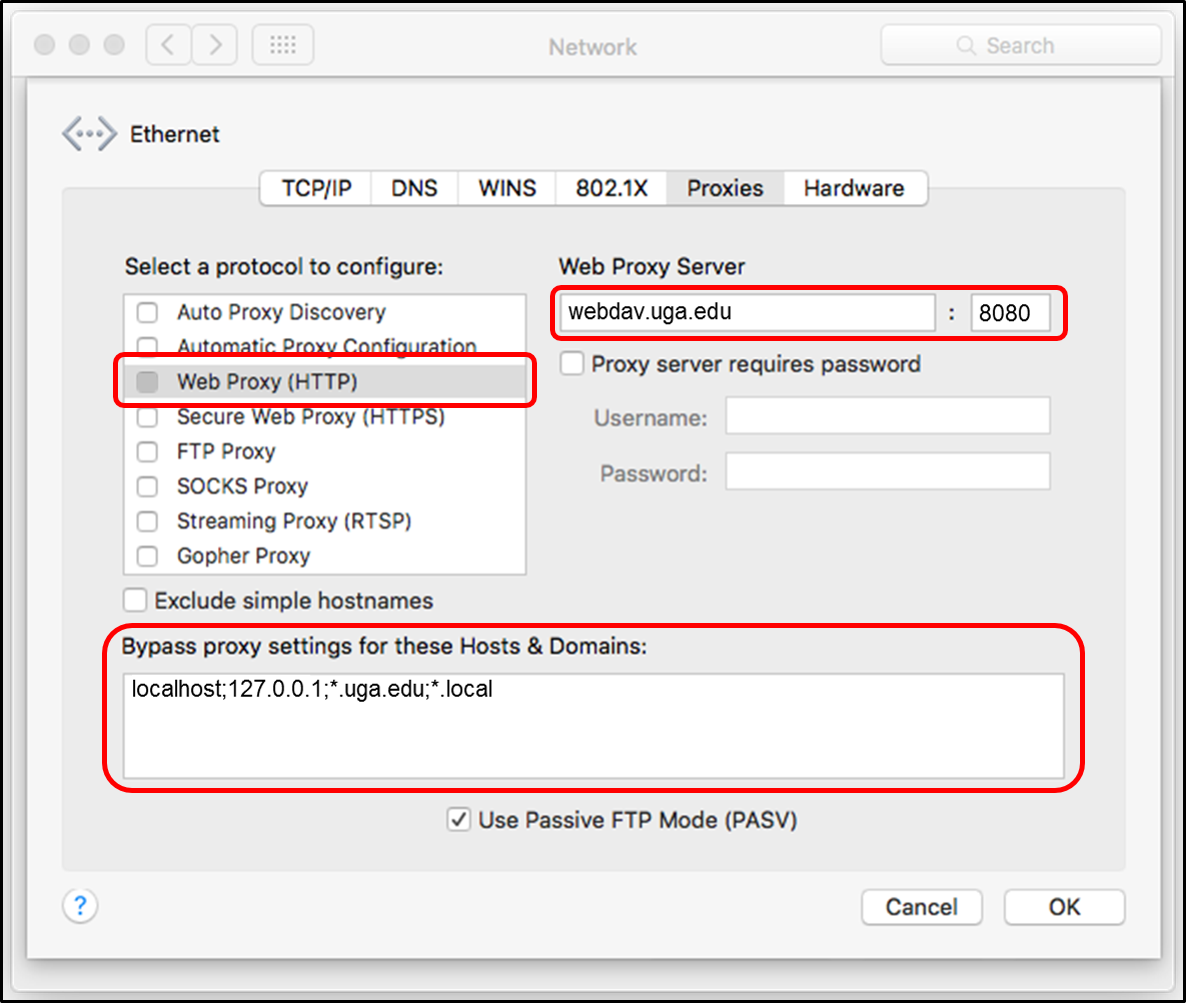
Mac System Proxy
- Combining the Search and Compare plugins, so that you can compare only specific responses
- Improving the fuzzer, adding ability to follow redirects, or to specify the number of threads to use. Also, adding the ability to define what is (or isn't) interesting in the fuzz results, and save only interesting conversations to the summary.
Extensibility
As a framework, WebScarab is extensible. Each feature above is implemented as a plugin, and can be removed or replaced. New features can be easily implemented as well. The sky is the limit! If you have a great idea for a plugin, please let us know about it on the list.
Project Contributors
The WebScarab project is run by Rogan Dawes. He can be contacted at rogan AT dawes.za.net
| PROJECT INFO What does this OWASP project offer you? | RELEASE(S) INFO What releases are available for this project? | |||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
| |||||||||||||||||||||||||||||||||||||||
Pages in category 'OWASP WebScarab Project'
The following 16 pages are in this category, out of 16 total.
C
G
H
O
P
W
Free Proxy For Mac
| Join hundreds of InfoSec professionals at our upcoming [Global AppSec DC, September 9-13] and [Global AppSec Amsterdam, September 23-27] |
The OWASP Zed Attack Proxy (ZAP) is one of the world’s most popular free security tools and is actively maintained by hundreds of international volunteers*. It can help you automatically find security vulnerabilities in your web applications while you are developing and testing your applications. Its also a great tool for experienced pentesters to use for manual security testing. ZAP 2.8.0 is now available!Please help us to make ZAP even better for you by answering the ZAP User Questionnaire!For a quick overview of ZAP see these tutorial videos on YouTube: For more videos see the links on the wiki videos page. Interested in a ZAP talk or training event? See the talks tab. Not one near you? Contact a Zap Evangelist to arrange one! For general information about ZAP:
For help using ZAP:
To learn more about ZAP development:
JustificationJustification for the statements made in the tagline at the top;) Popularity:
Contributors:
| Quick DownloadDonate to ZAPNews and EventsPlease see the News and Talks tabs Change LogCode RepoEmail ListQuestions? Please ask on the ZAP User Group Project LeaderProject Leader Co-Project Leaders Related ProjectsOpen Hub StatsClassifications
| |||
ZAP History Filter Screen Shot | ZAP Search Tab Screen Shot |
Upcoming Talks/Training:
For details of upcoming ZAP related talks or training please see the latest ZAP Newsletter
Latest News:
- 2019/06/07 Version 2.8.0 released
- 2018/07/26 The ZAP Heads Up Display (HUD) revealed at Bay Area OWASP meetup
- 2017/11/28 Version 2.7.0 released
- 2017/03/29 Version 2.6.0 released
- 2017/02/11 ZAP came second in the Top Security Tools of 2016 as voted by ToolsWatch.org readers
- 2016/06/03 Version 2.5.0 released
- 2016/05/26 ZAP bug bounty program launched
- 2016/02/23 ZAP declared the Top Security Tool of 2015 as voted by ToolsWatch.org readers
- 2016/02/19 ZAP February newsletter published
- 2016/01/04 ZAP January newsletter published
- 2015/12/15 ZAP December newsletter published
- 2015/12/04 Version 2.4.3 released
- 2015/11/02 ZAP November newsletter published
- 2015/09/07 Version 2.4.2 released
- 2015/07/31 ZAP Scripting Competition launched
- 2015/07/30 Version 2.4.1 released
- 2015/05/05 ZAP featured in the ThoughtWorks Technology Radar
- 2015/04/14 Version 2.4.0 released
- 2015/01/14 ZAP came second in the Top Security Tools of 2014 as voted by ToolsWatch.org readers
- 2015/01/02 ZAP Community Scripts repo launched
- 2014/05/21 Version 2.3.1 released
- 2014/04/10 Version 2.3.0 released
- 2014/03/10 Hacking ZAP blog post series started: http://zaproxy.blogspot.co.uk/2014/03/hacking-zap-1-why-should-you.html
- 2014/02/17 ZAP included as one of the SourceForge projects of the week
- 2013/12/20 ZAP declared the Top Security Tool of 2013 as voted by ToolsWatch.org readers
- 2013/11/04 ZAP Evangelists initiative launched
- 2013/10/29 Simon won Best Project Leader WASPY Award
- 2013/09/27 Version 2.2.2 released
- 2013/09/11 Version 2.2.0 released
- 2013/07/29 New language file including support for Bosnian
- 2013/06/17 ZAP user questionnaire launched, now in both English and Spanish
- 2013/06/05 ZAP questions can now be asked on irc
- 2013/05/10 5 ZAP related projects accepted for Google Summer of Code
- 2013/04/18 Version 2.1.0 released
- 2013/01/30 Version 2.0.0 released
- 2012/11/27 Started a new zaproxy-test project of unit and integrations tests
- 2012/10/29 Adopted Crowdin for translations
- 2012/10/22 Started generating weekly releases
- 2012/10/12 ZAP Overview tutorial video published
- 2012/09/18 ZAP Gear Store goes live
- 2012/08/05 Version 1.4.1 released
- 2012/07/08 Version 1.4.0.1 downloaded over 15,000 times
- 2012/07/05 Python API released
- 2012/06/15 ZAP accepted for the OWASP Project Reboot
- 2012/06/13 Using ZAP for Security Regression tests video published
- 2012/06/04 Version 1.4.0.1 downloaded over 10,000 times
- 2012/05/28 Simon's Introduction to ZAP talk at App Sec USA becomes the most watched OWASP video on vimeo
- 2012/04/23 3 ZAP related Google Summer of Code 2012 projects accepted. To find out how these are progressing please see their wiki pages.
- 2012/04/23 OWASP ZAP SmartCard Project officially launched.
- 2012/04/08 Version 1.4.0.1 released
- 2012/02/10 Version 1.3.4 downloaded over 10,000 times
- 2012/02/01 OWASP ZAP is named the Toolsmith Tool of the Year for 2011!
- 2010/09/06 The very first ZAP release, 1.0.0 announced via bugtraq
Yes, you can now buy ZAP related gear!
All of the artwork for ZAP swag is released under the Creative Common License and can be downloaded from the zap-swag repo.
You can of course use the artwork from this repo with any other online store that you like.
A range of products can be purchased from Redbubble
T-shirts can be purchased from Cafepress
ZAP is developed by a worldwide team of volunteers.
But we have also been helped by many organizations, either financially or by encouraging their employees to work on ZAP:
Some of ZAP's functionality:
- Traditional and AJAX spiders
- Web sockets support
- Authentication and session support
- Automatic updating option
Some of ZAP's features:
- Cross platform (it even runs on a Raspberry Pi!)
- Easy to install (using a multi-platform installer builder)
- Completely free (no paid for 'Pro' version)
- Ease of use a priority
- Fully internationalized
- Translated into over 20 languages
- Community based, with involvement actively encouraged
- Under active development by an international team of volunteers
ZAP is a fork of the well regarded Paros Proxy.
ZAP supports the following languages:
- English
- Arabic
- Bosnian
- Brazilian Portuguese
- Chinese
- Danish
- Filipino
- French
- German
- Greek
- Hungarian
- Indonesian
- Italian
- Japanese
- Korean
- Persian
- Polish
- Russian
- Sinhala
- Spanish
- Urdu
You can use Crowdin to help improve these translations or add new ones right now!
Release 2.6.0
ZAP 2.6.0 has been released, this is a bug fix and enhancement release
For more details see https://github.com/zaproxy/zap-core-help/wiki/HelpReleases2_6_0
Release 2.7.0
ZAP 2.7.0 has been released (Nov 2017), this is a bug fix and enhancement release
For more details see https://github.com/zaproxy/zap-core-help/wiki/HelpReleases2_7_0

It requires Java 8 (minimum) and supports Selenium 3.
Release 2.8.0
Proxy Settings Mac
ZAP 2.8.0 has been released (June 2019), this is a bug fix and enhancement release
For more details see https://github.com/zaproxy/zap-core-help/wiki/HelpReleases2_8_0
Proxy Server Mac
Involvement in the development of ZAP is actively encouraged!
You do not have to be a security expert in order to contribute.
Some of the ways you can help:
Feature Requests
Please raise new feature requests as enhancement requests here: https://github.com/zaproxy/zaproxy/issues
If there are existing requests you are also interested in then please 'star' them - that way we can see which features people are most interested in and can prioritize them accordingly.
Feedback
Please use the zaproxy-users Google Group for feedback:
- What do like?
- What don't you like?
- What features could be made easier to use?
- How could the help pages be improved?
Log issues
Have you had a problem using ZAP?
If so and its not already been logged then please report it
Localization
Web Proxy Tool For Mac
Are you fluent in another language? Can you help translate ZAP into that language?
You can use Crowdin to do that!
Development
If you fancy having a go at adding functionality to ZAP then please get in touch via the zaproxy-develop Google Group.
Again, you do not have to be a security expert to contribute code - working on ZAP could be great way to learn more about web application security!
If you actively contribute to ZAP then you will be invited to join the project.